Estimated reading time:3 minutes
In May, a new malware exploiting Microsoft Office software called Follina was discovered. This malware exploits the Microsoft Office security vulnerability CVE-2022-30190 to execute malicious code on the victim's device. Specifically, the attacker creates a malicious Word file and transfers this file to the target machine. When the victim downloads and opens the file, the malicious code will run and allow the hacker to attack.
The Microsoft Office vulnerability CVE-2022-30190 is a vulnerability with a CVSS security score of 7.8 – a high score – indicating that it is a dangerous vulnerability. At the same time, Microsoft Office is also one of the most used software today, estimated to have over 1 billion users worldwide. Therefore, it is necessary to quickly fix this security hole and prevent Follina malicious code from attacking the system.

Up to the present time, there are 5 affected versions of Microsoft Office, which are Office 2013, 2016, 2019 and 2021. There is still no patch of Office that allows to fix this vulnerability. To prevent this vulnerability, it is possible to simulate the Microsoft Office Follina attack on the system and study to create a Signature.
Interested businesses and organizations can use the Picus Security attack emulator for Follina malware emulation. This is a solution that allows to simulate the latest and most dangerous cyber attacks safely and effectively, helping businesses evaluate the security of the system as well as research to create a Signature and IoC for malicious code.
With Follina, Picus simulates all attack steps from transmitting malicious code to executing malicious code on the victim's device:
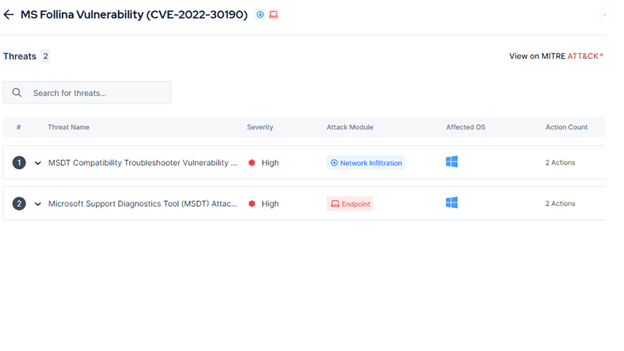
Network Infiltration: This is the step of transferring malicious code to the victim's machine in the Network environment. Picus can simulate the transmission of malicious code over protocols such as http, https or via Email.
Endpoint Execution: This is the step that executes malicious code on the Endpoint device. If successful, the victim's machine will be hacked by the Hacker and execute the malicious code.
To prevent MS Follina attacks, businesses can use the Fidelis XDR solution. This is a solution that combines EDR, NDR and Deception, allowing comprehensive protection of enterprise systems from the most dangerous attacks such as APT, Data Theft, Malware, Ransomware, Phising, C&C attacks, etc.
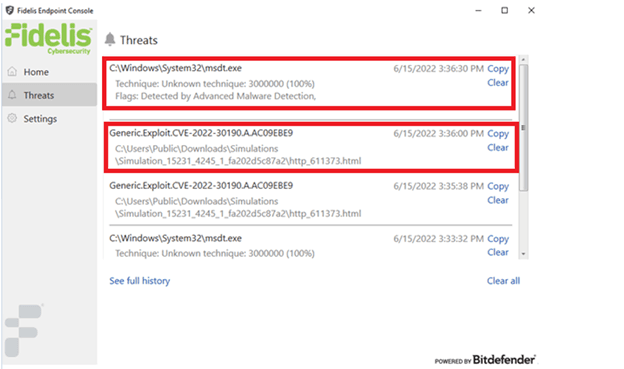
When Picus emulated MS Follina on an Endpoint protected by Fidelis Agent, all attacks were all intercepted:
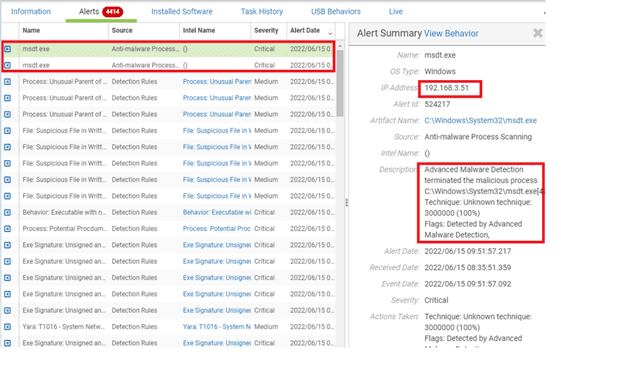
- The malicious file containing the malicious code http_611373.html was intercepted by Fidelis after being downloaded by the user's computer.
- Malware's msdt.exe is also blocked by Fidelis when trying to execute.
On the Fidelis admin interface, you can view details related to the attack such as the victim's IP, the path of the malicious code, the time of the attack, the attack technique, etc.