Estimated reading time:5 minutes
A critical remote code execution vulnerability was found in Atlassian Confluence Server and Data Center with a CVSS score of 9.8 (Critical). CVE-2022-26134 is an OGNL injection vulnerability that a malicious threat actor can exploit to run arbitrary commands in a target Confluence Server or Data Center. Since the vulnerability affects all versions released before the vulnerability’s discovery, organizations are advised to update their Confluence Server and Data Center as soon as possible. For detailed information, visit our blog posts.
June’s Threat Actors
ToddyCat Threat Group
- Picus Threat ID: 311440,262389,882906
- Target Regions: Taiwan, Viet Nam, Afghanistan, India, Iran Islamic Republic of, Malaysia, Pakistan, Russian Federation, Slovakia, Thailand, United Kingdom of Great Britain and Northern Ireland
- Malware (Tool): Samurai
GALLIUM Threat Group
- Picus Threat ID: 863399,443799,579576
- Codename: Operation Soft Cell
- Aliases: Operation Soft Cell Target Regions: Viet Nam, Russian Federation, Philippines, Mozambique, Malaysia, Cambodia, Belgium, Australia, Afghanistan
- Target Industries: Financial, Telecommunication, Finance, Government, Telecommunications
- Malware (Tool): PingPull RAT
Mustang Panda Threat Group
- Picus Threat ID: 701360,672136,786785
- Aliases: TA416, RedDelta, BRONZE PRESIDENT
- Target Regions: Russia
- Target Industries: Government
- Malware (Tool): PlugX
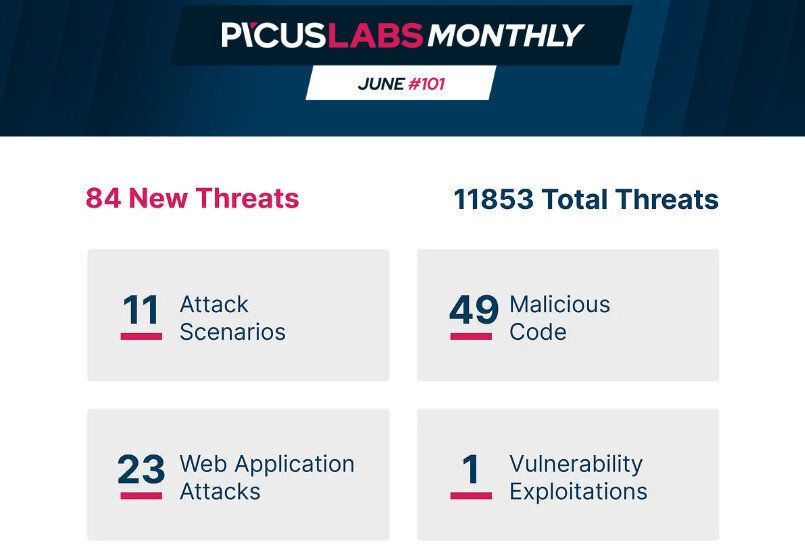
Attack Scenarios
- APT / Malware Scenarios
- BlackCat Ransomware Scenario
- Picus Threat ID: 652923
ACTION
1. Create Scheduled Task by using Alternate Data Streams (ADS) ATT&CK Technique: T1053 Scheduled Task/Job
ATT & CK: Execution, Persistent, Privilege Escalation
2. Execute Commands by using Image File Execution Options ATT&CK Technique: T1546 Event Triggered Execution
ATT&CK Tactics: Privilege Escalation, Persistence
3. Add a Local Admin Account
ATT&CK Technique: T1136 Create Account
ATT & CK Tactic: Persistent
…
13. Write a File that Contains BlackCat Ransom Note and Open It ATT&CK Technique: T1491 Defacement
ATT&CK Tactic: Impact
Atomic Attacks
Command Execution via Microsoft Support Diagnostics Tool (MSDT) by serving HTML Payload
- Picus Threat ID: 322606
- T1055ATT&CK Technique: T1055 Process Injection
- ATT&CK Tactics: Execution
Beacon Memory Obfuscation by using DeepSleep Variant
- Picus Threat ID: 540508
- ATT&CK Technique: T1027 Obfuscated Files or Information
- ATT&CK Tactics: Defense Evasion
In-memory .NET Assembly Execution by using Reflective DLL Injection
- Picus Threat ID: 895925
- ATT&CK Technique: T1055 Process Injection
- ATT&CK Tactics: Defense Evasion
Malicious Code Mustang Panda Threat Group’s Malware
- Picus Threat ID: 701360,672136,786785
- Signature ATT&CK Technique: T1140,T1105,T1574,T1566,T1059
- Target Regions: Russia
- Target Industries: Government
Vice Society Threat Group’s Malware
- Picus Threat ID: 451171
- Signature ATT&CK Technique:T1106,T1547.001,T1055,T1057,T1074,T1129
- Target Regions: Italy, USA
- Target Industries: All
ToddyCat Threat Group’s Malware
- Picus Threat ID: 311440,262389,882906
- Signature ATT&CK Technique: T1073,T1037,T1071.001,T1090,T1055,T1053
- Target Regions: Taiwan, Viet Nam, Afghanistan, India, Iran Islamic Republic of,Malaysia, Pakistan, Russian Federation, Slovakia, Thailand, United Kingdom of Great Britain and Northern Ireland
- Target Industries: All
Web Application Attacks Atlassian Confluence Data Center Remote Code Execution Vulnerability
- Picus Threat ID: 890767
- OWASP Top 10: A3 – Injection
- CVSS 3 Base Score: 9.8 Critical
- CVE: CVE-2022-26134
- Affected Product: Atlassian Confluence Data Center
Zimbra CRLF Injection in Memcached Lookups Vulnerability
- Picus Threat ID: 5377866
- OWASP Top 10: A3 – Injection
- CVSS 3 Base Score: 7.5 High
- CVE: CVE-2022-27924
- Affected Product: Zimbra
Collaboration Magnolia CMS YAML Deserialization Vulnerability
- Picus Threat ID: 894029
- OWASP Top 10: A8 – Software and Data Integrity Failures
- CVSS 3 Base Score: 7.8 High
- CVE: CVE-2021-46364
- Affected Product: Magnolia CMS
Vulnerability Exploitations
Linux Netfilter Elevation Privilege Vulnerability Variant-2
- Picus Threat ID: 718837
- CVE: CVE-2022-1972
- CVSS 3 Base Score: 7.8 High
- Affected Product: Linux Kernel 5.13
Sigma Rules
Signed Binary Proxy Execution via WorkFolders.exe
- Picus Sigma ID: 8046
- Technique: System Binary Proxy Execution
- Tactic: Defense Evasion
Suspicious Execution of MSDT Process
- Picus Sigma ID: 3382
- Technique: System Binary Proxy Execution
- Tactic: Defense Evasion
Dump LSA Secrets from the Registry Picus
- Sigma ID: 6408
- Technique: OS Credential Dumping: LSA Secrets
- Tactic: Credential Access


